About IGLU
Unlocking the Power of Technology
Our approach to technology is human-centric. That means we put the human at the centre of everything we do – from delivering premium support, through managing and enhancing business applications, to providing virtual CTO, CIO and CISO services, and of course; communicating in simplistic and realistic language.
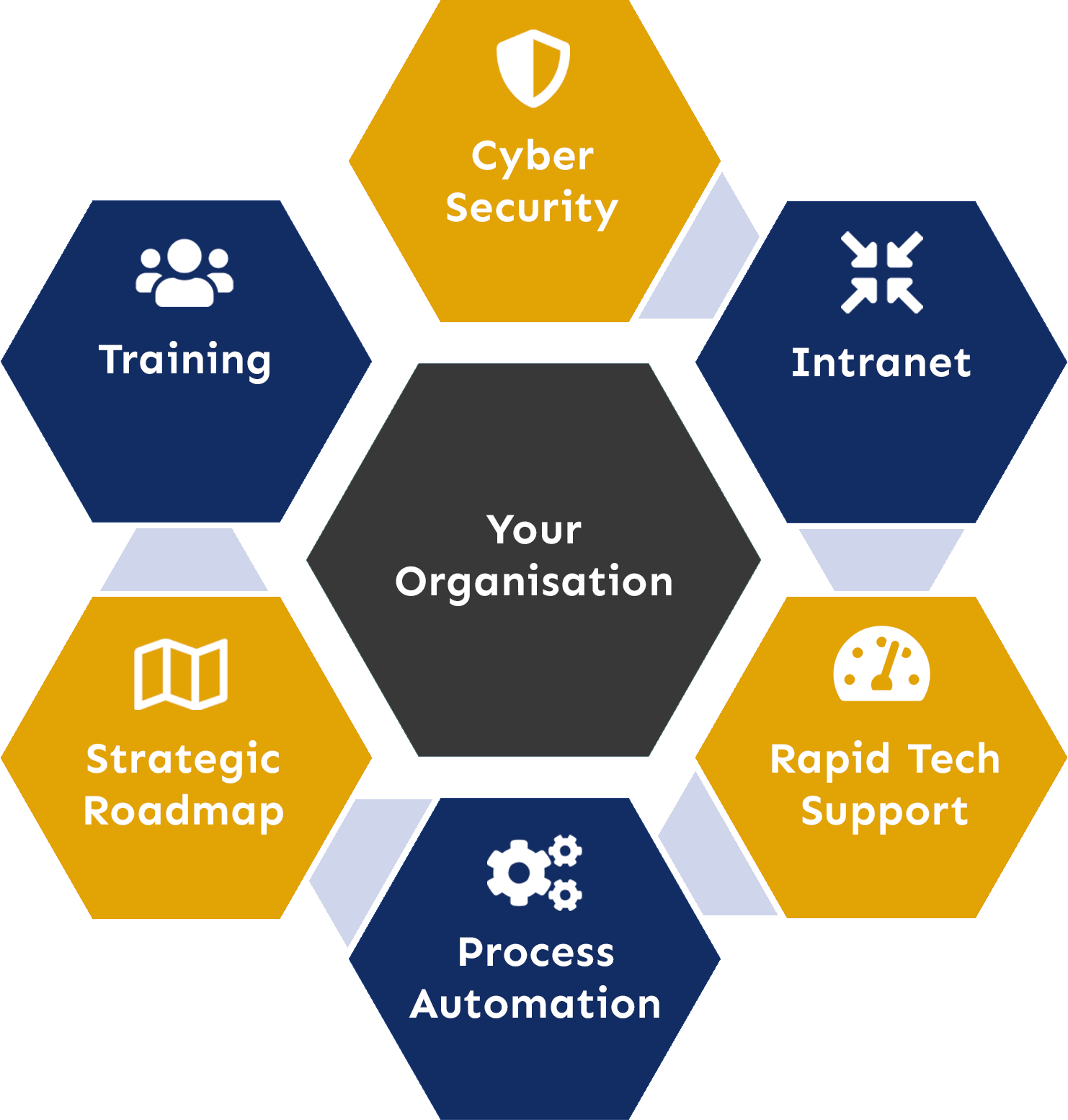
We believe that technology only becomes useful when it is used, by you and your colleagues, to change enhance/improve the way you do something; automation of operational processes – onboarding and inductions, document approvals and more, simplicity in doing your day-to-day roles, centralised & collaborative information management, engaging with your own customers. Technology can empower your entire world.
Our values
Learn more about our values that keep us grounded and focussed on you.
Our Journey
Starting out as a very small team, and part of a larger organisation, the iglu. story is an interesting, and never boring one!

Formation of Iglu
Early in the lifecycle of any business, it’s easy to keep your small team focussed on your goals and principles. As an organisation grows, that important message can become diluted. Learn more about our values that keep us grounded and focussed on you.

ISAAC Intelligence Limited
Established in 2013 and born in the cloud. Specialising in Microsoft 365 and SharePoint solutions, ISAAC was created to help organisations benefit from cloud technologies and early-stage digital transformation.

Guidance Technologies Limited
Established in 2009, Guidance has been a leading light in IT Managed Services ever since. Specialising in highly proactive and innovative IT solutions for a wide variety of rapidly growing and ambitious organisations.

